From https://www.safetydetectives.com/blog/robert-dickerson-virnetx/
SafetyDetectives spoke with Robert Dickinson, Director of Product Innovation and Strategy at VirnetX. We talked about the different services offered by VirnetX, Zoombombing and how you can avoid it, potential cybersecurity threats, and tips for securing your network.
Can you please introduce yourself, and talk about your background and your role at VirnetX?
Robert Dickerson is the Director of Product Innovation and Strategy at VirnetX (NYSE: VHC). VirnetX is an Internet security and technology company that was founded in 2005.
As Director of Product Innovation and Strategy, I’m responsible for driving product innovation and executing product initiatives to create security solutions for our customers and partners.
What does VirnetX specialize in, and what are your flagship services?
At VirnetX, we are committed to preventing cyberattacks. VirnetX strives to prioritize user safety with private and secure virtual environments because these elements are vital for maintaining business continuity. Below are VirnetX’s core products and services:
- VirnetX One™ is VirnetX’s flagship SaaS-based platform and offers organizations comprehensive protection and security. VirnetX One™ features seamless activation and provisioning of a zero-trust enabling platform that provisions a dynamic credential-based network. VirnetX One™ provides full control and protection of an organization’s sensitive information and intellectual property. VirnetX One™ enables organizations to gain visibility and insight into how information is being used, accessed and streamlined. VirnetX One™ features real-time network information, actionable value and solid ROI
- War Room delivers a closed and private video conferencing and meeting solution that secures the exchange and privacy of information between trusted parties without fear of eavesdropping or data breaches. War Room works on all devices so employees can seamlessly participate in meetings while working remotely or in the office. Secured by the VirnetX One platform, War Room is built on VirnetX Secure Domain Names and patented technology, giving businesses protection, control, and visibility to secure its communications.
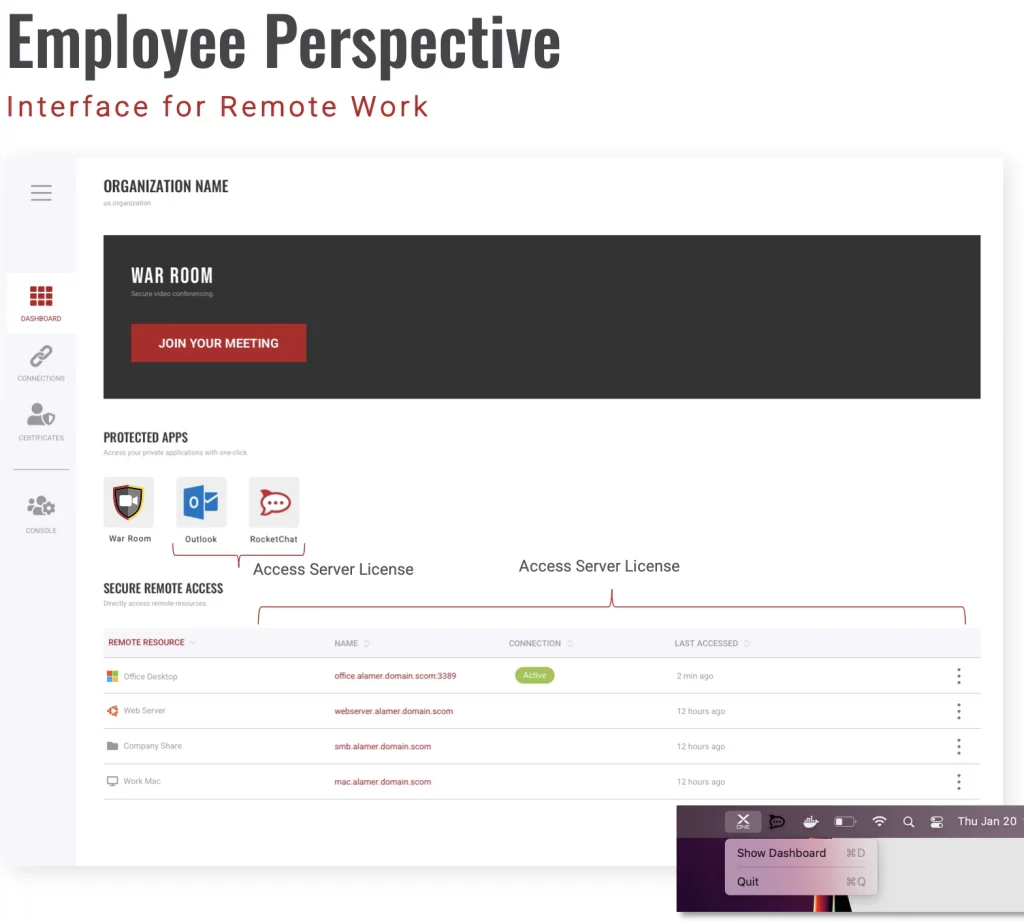
The War Room interface
- Built on the VirnetX One platform, Matrix enables enterprises to defend hybrid-remote workers from security threats that will drive workforce efficiencies, scale operations, and maintain business continuity. By equipping corporate applications to be invisible from unauthorized users, Matrix protects contemporary workforces from sophisticated hackers and mitigates threats. Matrix provides Zero Trust Network (ZTNA) to applications and infrastructures, flexible end-to-end encryption, and unique secure domain names identities.
Can you explain how War Room prevents Zoombombing?
From corporations such as Peloton to celebrities like Olivia Munn, enterprises and consumers have been victims of being “Zoombombed.” VirnetX is answering the call with War Room to mitigate threats and protect users from a potential cyber pitfall. As the industry’s most secure video conferencing solution, War Room elevates today’s remote workforce by providing secure video conferencing with a comprehensive security posture to prevent cyber attackers from accessing critical and sensitive information.
With War Room, meeting links are only accessible by authorized and authenticated participants given access by the meeting host. Thus, Zoombombing is eliminated, because just knowing the meeting link does not give an individual access to the meeting. For unauthorized participants, the meeting does not exist. They will be automatically blocked from joining and will not have access to the meeting topic or participants through the meeting link itself. War Room’s alternative approach is to eliminate all public access. Unfortunately, other third-party video conferencing solutions create features like waiting rooms to give a false sense of meeting security. Instead of enforcing all participant authentication and creating a truly secure meeting, they instead force the host to filter out unwanted participants at the start of every meeting.
Other than Zoombombing, what are some cybersecurity concerns with online meetings?
With the rise of the hybrid workforce, the threat of remote attacks is at an all-time high. According to IBM, the average cost of a data breach in the US is $9.4M. While breaches can be costly, diffusing Zoombombing and other destructive threats has never been more critical for businesses. Without secure video conferencing, the consequences can be dire. For example, Zoombombing and other attacks can significantly harm a corporation’s reputation and financial bottom line.
Do you have tips or advice for remote workers to secure their data and network from hackers?
Incorporating robust security measures are the best way for a company to protect its attack surface and prevent costly incidents. Here are some best practices:
- Remove the attack surfaces: Eliminate public Internet access and exposure to business applications, services and infrastructure. Protection of these key use cases is critical since they are the top targets for threat actors and represent key entry points to access sensitive and confidential business information.
- Encrypt your data: Phishing attacks are detrimental and costly. To combat phishing attacks, it’s crucial for organizations to ensure that employee data can’t be accessed by cyber thieves trying to misuse company data. Leveraging encryption safeguards employee data from a potential breach.
- Guarantee data access is secure: Many enterprises don’t deploy a Zero Trust architecture. Adopting a Zero Trust policy can restrict and segment access to an organization’s confidential assets and sensitive information.
- Monitor user activity: Gain visibility into the users and devices accessing your data and networks. Today’s modern and innovative security solutions can prevent a pitfall and breach before it happens.


